The South Korean National Police Agency sounded an alarm Tuesday for a targeted campaign from the North Korean hacker groups aimed at stealing the country’s defense technology.
The announcement disclosed multiple successful breaches of hacking groups Lazarus, Andariel, and Kimsuky, which are all linked to Pyongyang’s stealthy hacking cartel. Exploiting vulnerabilities in both primary targets and their subcontractors, these groups planted malware capable of siphoning off valuable technological data.
North Korean hacker groups directly infiltrated defense industry companies, hacked defense industry partners with relatively weak security, stole the defense industry company’s server account information, and then infiltrated major servers with malware, the police announcement said.
The findings came from a joint operation by the National Police Agency and the Defense Acquisition Program Administration, which unearthed a series of compromises dating back to late 2022. Many affected companies were unaware of the breaches until authorities intervened.
North Korean hackers have a common goal of stealing defense technology and are conducting an all-out attack by deploying multiple hacking groups in this campaign, making their attack methods more elaborate and diverse, the police agency said.
North Korean Hacker Groups Use Diverse Tactics
The police report delineates three distinct cases, each illustrating the diverse tactics employed by the hacking groups to pilfer defense-related technology.
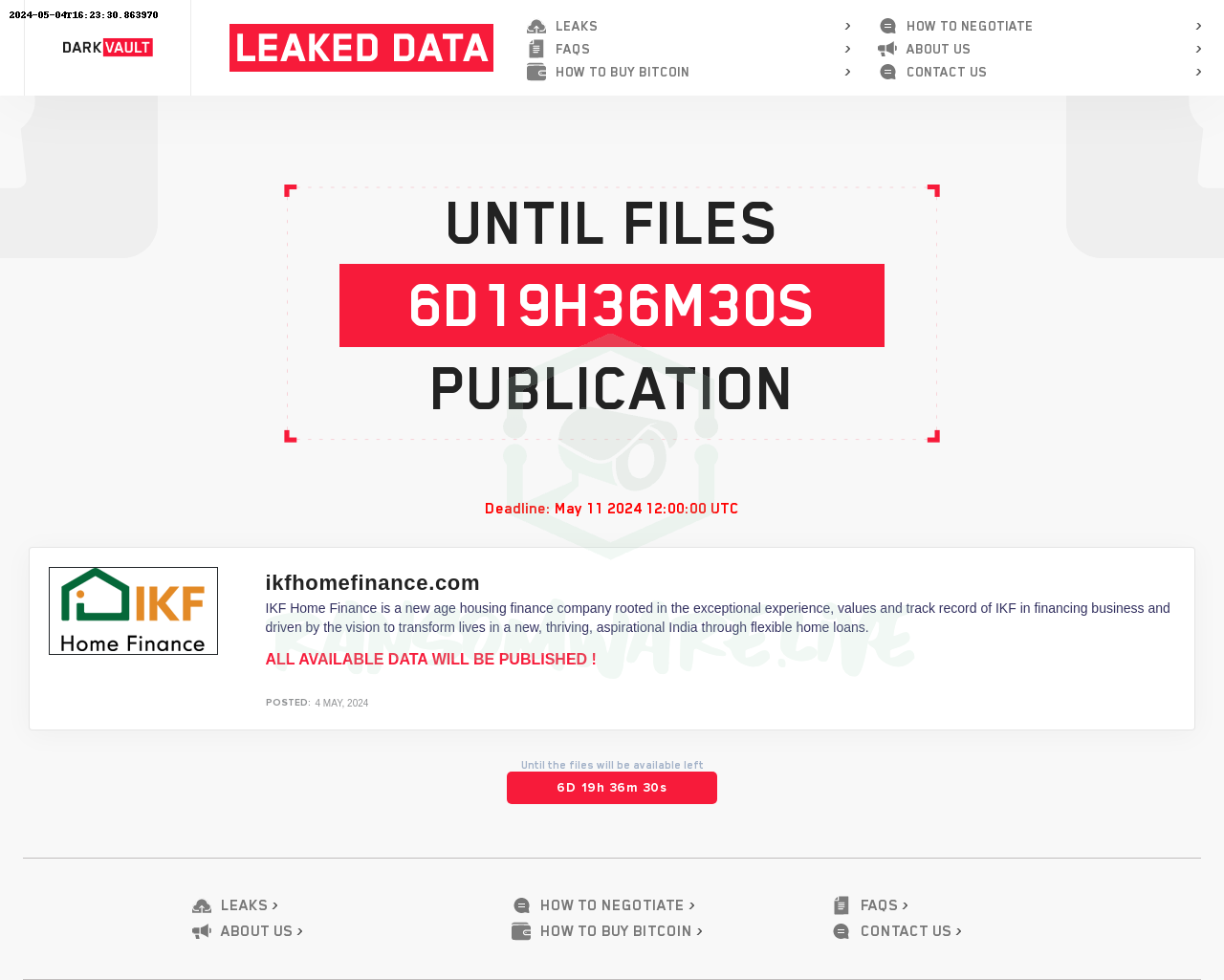
In one instance the Lazarus hackers breached a defense company’s networks in November 2022 by exploiting loopholes in their network management. They targeted an external network server, infected it with malware, and leveraged an open port meant for testing to infiltrate the internal network. This allowed them access to sensitive data stored on employee computers, which they then exfiltrated to an overseas cloud server.
The breach affected six computers, and evidence of the data leak was identified through analysis of both the victim company’s systems and the overseas servers.
Lazarus hacker group’s attack chain. Credit: National Police Agency of South KoreaLazarus hacker group’s attack chain. Credit: National Police Agency of South Korea
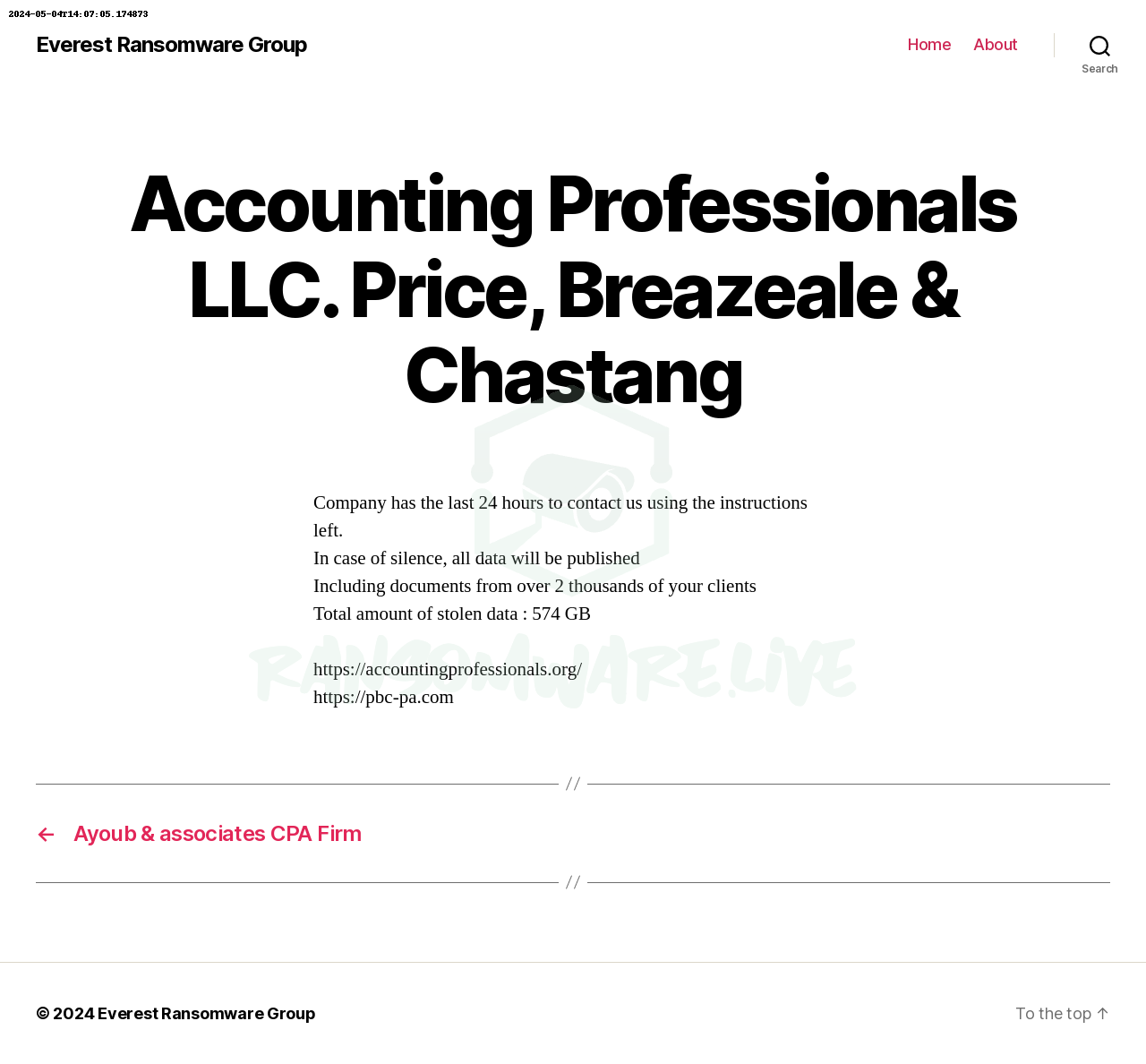
In the second case the Andariel hacker group gained access to defense industry data by compromising an employee account, which maintained servers for a defense industry partner. By injecting malicious code into the partner’s servers around October 2022, they were able to extract and leak stored defense technology data. This breach exploited a loophole in how employees used their personal and professional email accounts for official system access.
Andariel hacker group attack chain. Credit: National Police Agency of South KoreaAndariel hacker group attack chain. Credit: National Police Agency of South Korea
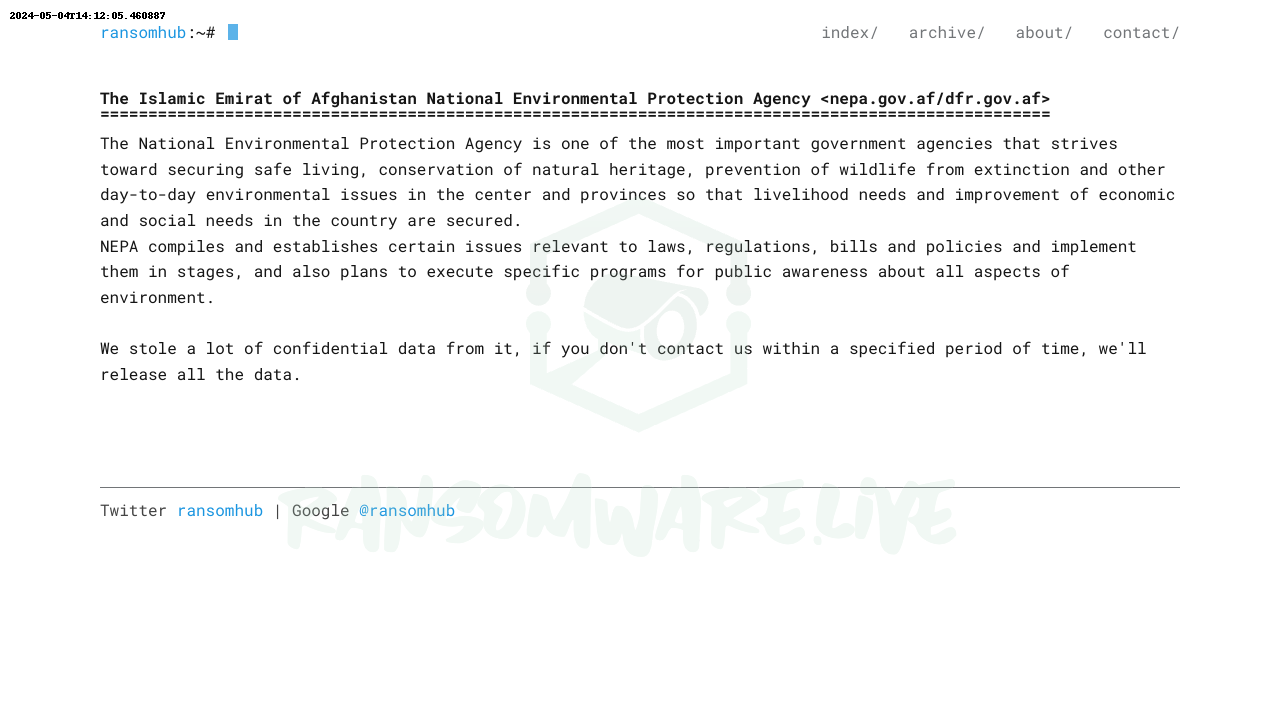
Lastly, Kimsuky seized upon a vulnerability in a defense subcontractor’s email server between April and July 2023. T Over several months, they stole technical data by exploiting a flaw that allowed the download of large files sent via email from external sources without requiring login credentials. This method bypassed security measures, enabling the hackers to access and extract sensitive information undetected.
Kimsuky hacker group’s attack chain. Credit: National Police Agency of South KoreaKimsuky hacker group’s attack chain. Credit: National Police Agency of South Korea
The National Police Agency said, “It is expected that North Korea’s hacking attempts targeting defense technology will continue, so not only defense companies but also partner companies must separate internal and external networks, change email passwords periodically, and set up account authentication such as two-step authentication.”
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.

Leave a Reply