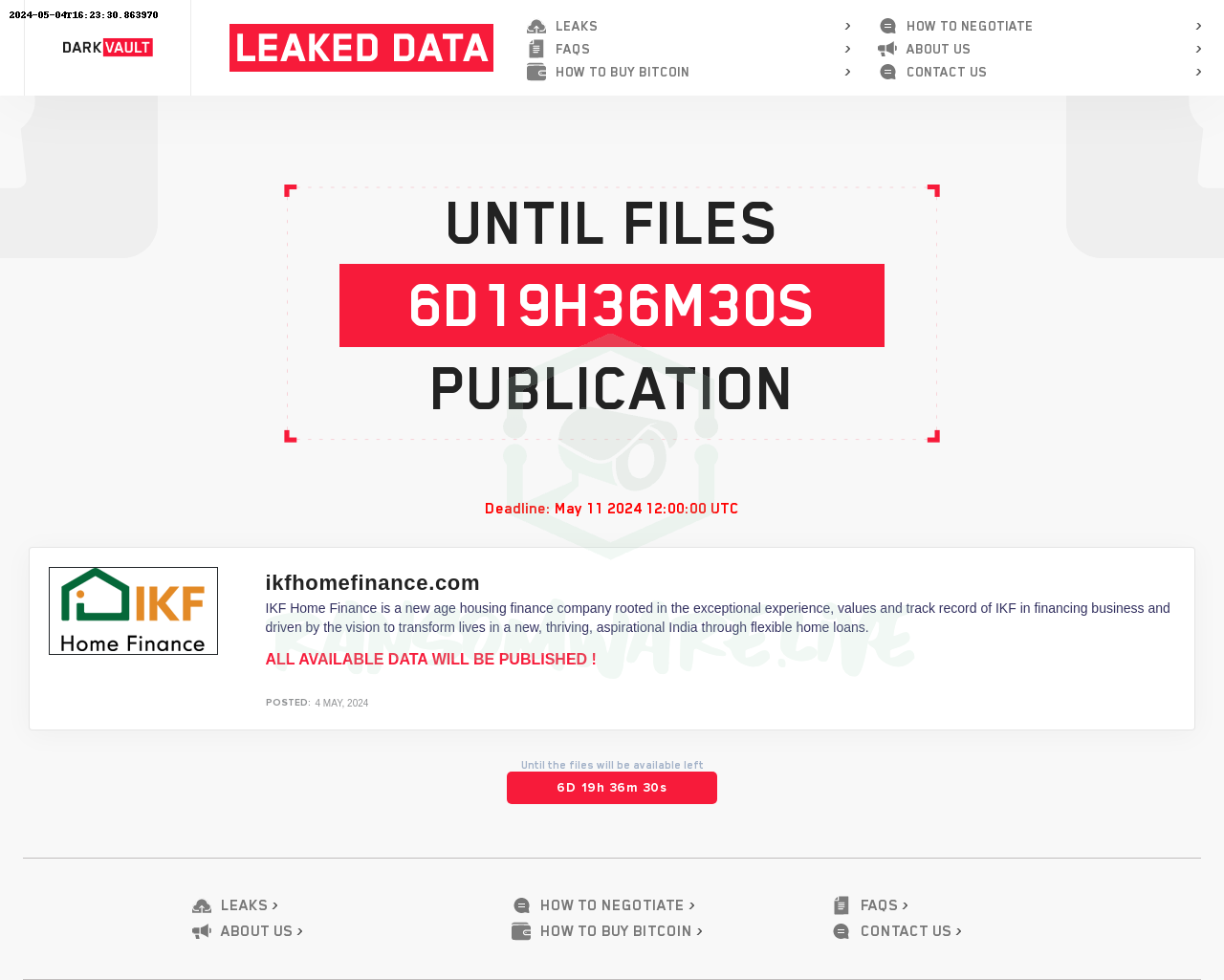
Central Power Systems & Services, a major distributor of industrial and power generation products in Kansas, Western Missouri, and Northern Oklahoma, has fallen victim to the notorious Hunters Ransomware Group.
The cyberattack on Central Power Systems & Services, disclosed by the ransomware group, has raised concerns about the safety of sensitive data and the integrity of critical infrastructure.
Central Power Systems & Services, the sole authorized distributor for Allison Transmissions, Detroit Diesel, MTU, Doosan, and Liebherr in the region, has been a stalwart in serving commercial equipment needs since 1954.
However, the recent alleged cyberattack may have halted its official website as it displayed a disconcerting message: “Sorry you have been blocked. You are unable to access cpower.com.”
Uncertainty About Cyberattack on Central Power Systems & Services
The claim by the Hunters Ransomware Group has yet to be officially confirmed, leaving both the company and its clients in a state of uncertainty. While attempts to access the website raise suspicions, the possibility of a technical glitch cannot be ruled out until an official statement is released.
If proven true, the implications of this Central Power Systems & Services cyberattack could be significant. The potential compromise of sensitive data poses a serious threat not only to the company but also to its clients and partners. With no details provided by the ransomware group regarding the extent of the breach or the nature of compromised data, the situation remains tense.
Previous Incidents
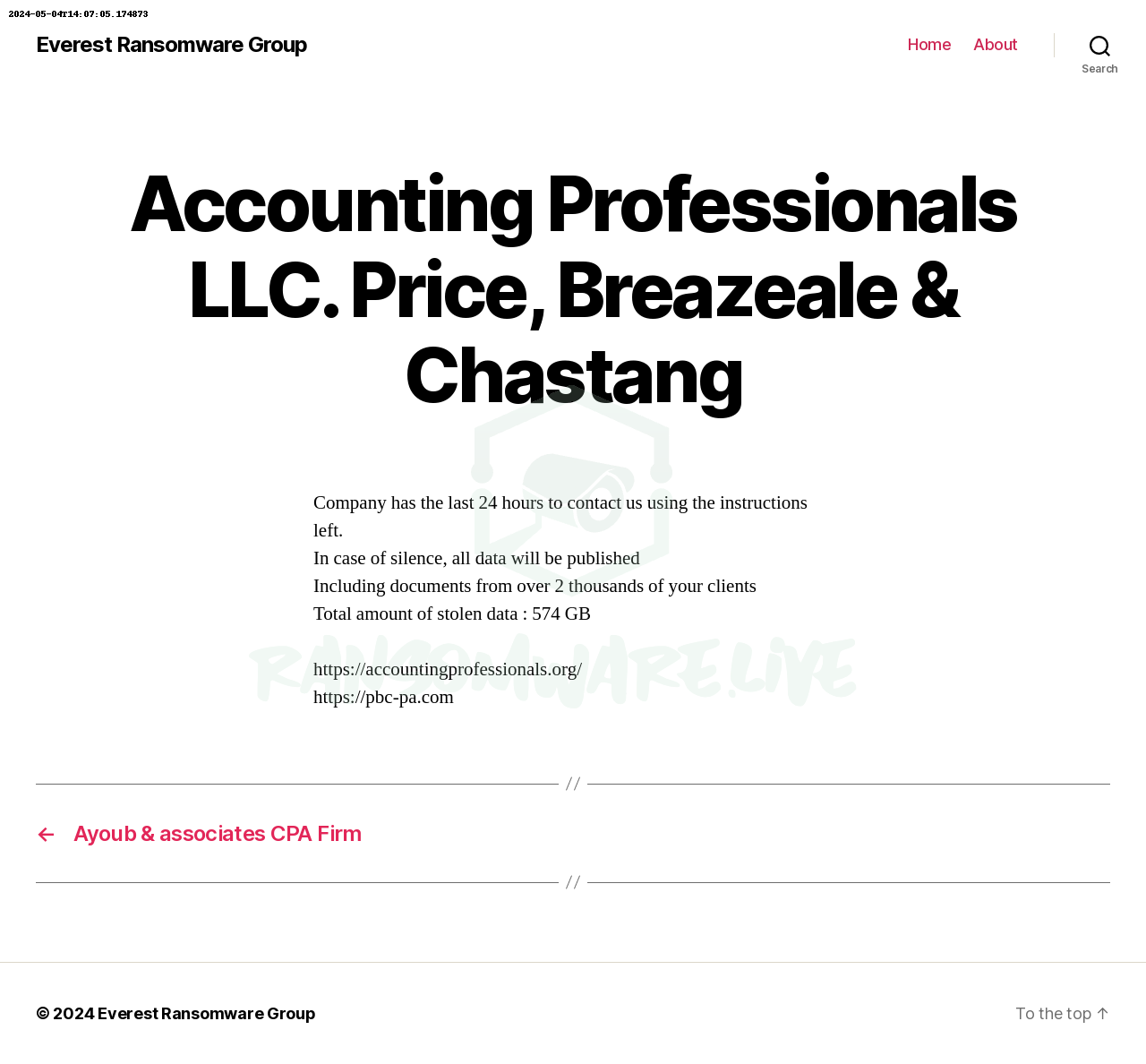
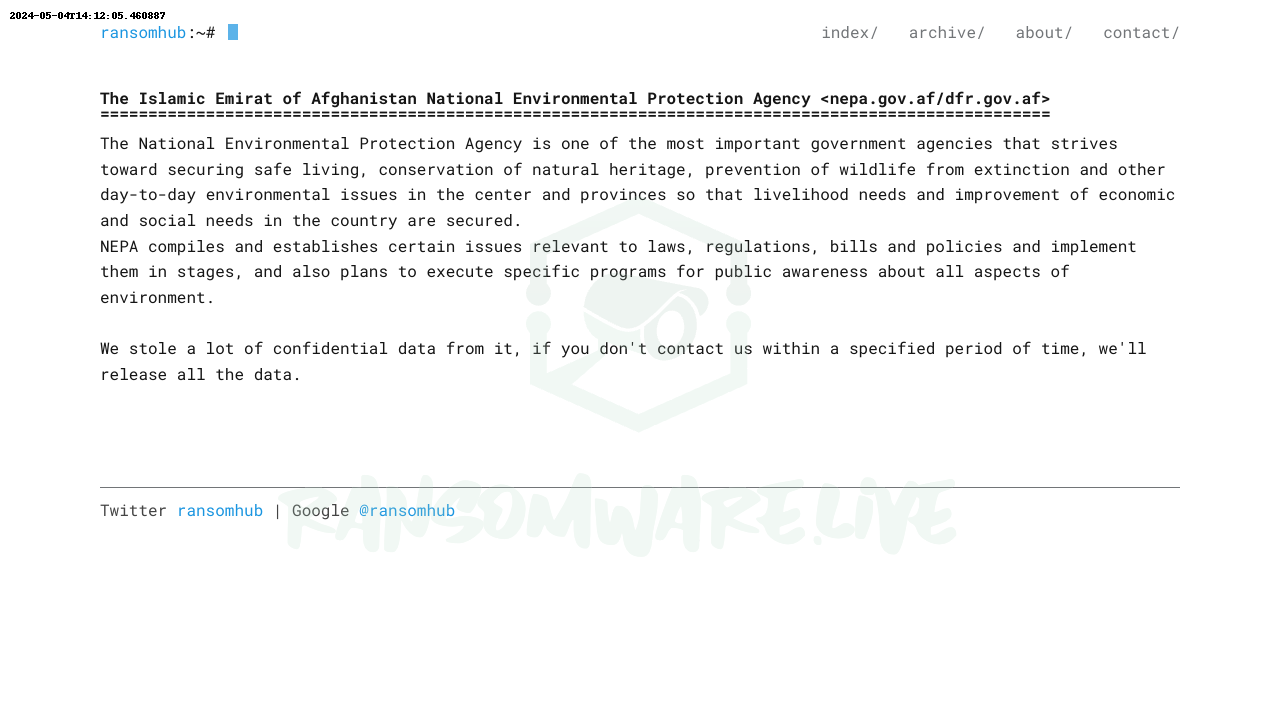
This is not the first time the Hunters Ransomware Group has made headlines. Before this, the group targeted various organizations across different sectors and countries. In 2024 alone, the group claimed responsibility for cyberattacks on the Dalmahoy Hotel & Country Club in the UK, Double Eagle Energy Holdings IV, LLC in the US, and Gallup-McKinley County Schools in New Mexico, among others.
The modus operandi of the Hunters Ransomware Group involves encrypting files and appending the “.LOCKED” extension, followed by demands for ransom in exchange for decryption keys. Additionally, the group often leaves instructions for negotiation in files named “Contact Us.txt” within compromised directories.
The cyberattack on Central Power Systems & Services highlights the growing threat posed by ransomware groups to organizations worldwide. With cybercriminals continuously evolving their tactics and targeting critical infrastructure, businesses must remain vigilant and prioritize cybersecurity measures.
As the investigation into this cyberattack continues, stakeholders await an official statement from the company regarding the breach and its impact. Until then, the industry remains on high alert, bracing for potential fallout from yet another audacious move by the Hunters Ransomware Group.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.

Leave a Reply